How to Create Guest Access Portal for External Users Management – Part 1
- Radhakrishnan Govindan
- Jun 8, 2019
- 3 min read
In this Article Series, We are going to see how to create Custom application Portal for the Guest Users Management.
This Portal helps to Guest Users to request from External Domains or External World.. Post request received, Guest Inviter Administrators can login and approve the requests. Also it helps in auto approving the Domains and also manage the groups that users should be part once added to apply the custom Conditional Access Policies and other requirements.
To get this portal hosted, We are going to use the following Services from Azure,
Azure Active Directory application registrations.
Azure App Services
Azure Cosmos DB
We should have appropriate Azure Subscriptions for the above services to get this application hosted and configured successfully.
Okay.. Let’s get started
1. Creating Azure Applications using Azure Active Directory
Login to https://portal.Azure.com — Azure Active Directory— App Registrations and click on New Application Registration
Note: I have used legacy option, if you’re comfortable with new App registration options, you still can go with that as well.
Enter the Name for the application, Select Application type : Web app/API and sign-on URL as https://willentertheurl-Later
This Sign-on URL we are going to change later in this stage with right url, so type with anything for now since it is mandatory to move further from here.

Once application Registration done, click on Settings

Click on Required Permissions

Click on Add
Click on Select an API
Select Microsoft Graph
Click “Select permissions“. On the “Enable Access” panel that appears, check the following items:
APPLICATION PERMISSIONS
Read and write directory data
Read and write all users’ full profiles
DELEGATED PERMISSIONS
Sign in and read user profile
Once all set as mentioned, Click on Done
Click on Grant Permissions

Click on Yes to Grant Permissions

Now, we need to generate the keys,
Clock on Keys– Type Key1 in the description and select the Years for expiration and click on Save

Copy the keys generated, once you moved out of this blade, you will not get it back, hence ensure rightly copied and saved for our use in the later stage

Now, Admin application registration completed, we need t register once more application for Pre-Auth Approval.
Again, Go to Azure Active Directory —App registration— click on New application Registration

Enter the Name B2B Pre-Authentication App, Application type : Web app / API, Sign-on URL: https://willenterthisURL-Later
This Sign-on URL we are going to change later in this stage with right url, so type with anything for now since it is mandatory to move further from here.

Click on Settings

Select Required Permissions and click on Add

Select Microsoft Graph
Under “Required permissions”, you will again add the Microsoft Graph API. This time you only need to check one item:
DELEGATED PERMISSIONS
Sign in and read user profile

Click on Done

Click on Grant Permissions

Click on Yes to enforce the permissions

Now, we need to generate the keys for Pre-Auth Application as well
Click on Keys– Type Key1 in the description and select the Years for expiration and click on Save

Copy the keys generated, once you moved out of this blade, you will not get it back, hence ensure rightly copied and saved for our use in the later stage

Go to the Properties and Select Multi-Tenanted as Yes
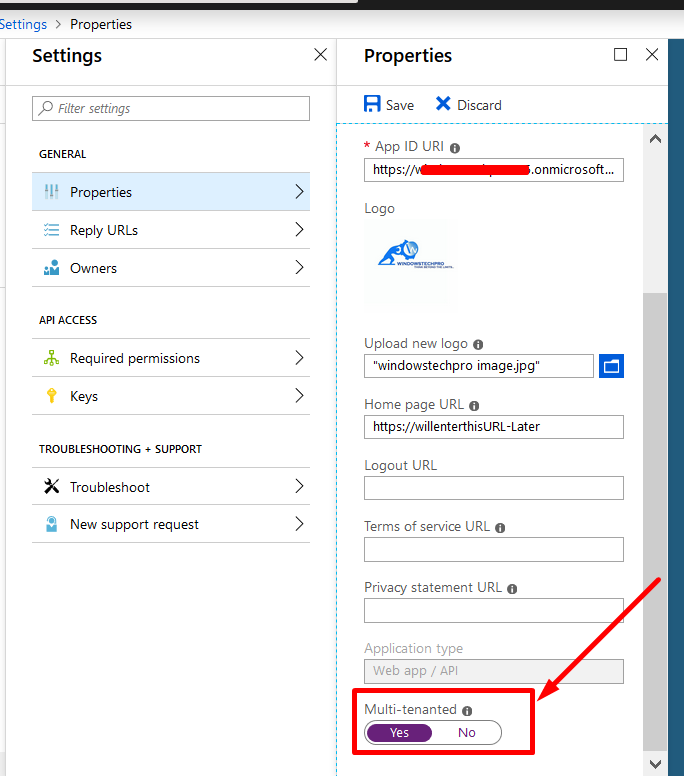
Go back and select Manifest of the B2B Pre-Authentication app and search for oauth2AllowImplicitFlow and set it as true and click on Save

Now, you need to copy of the application IDs of the Admin app and Pre-Auth App and keys which generated. you also need to copy the tenant ID from the directory properties.
So far, we have 5 values copied and applications are registered.

In next article, We will see how to deploy Application using Azure App Services and CosmosDB.
For the Part 2 Article in this series, How to Create Guest Access Portal for External Users Management – Part 2















Comments